“John the Ripper” – is a fast password cracker. Its primary purpose is to detect weak Unix passwords.
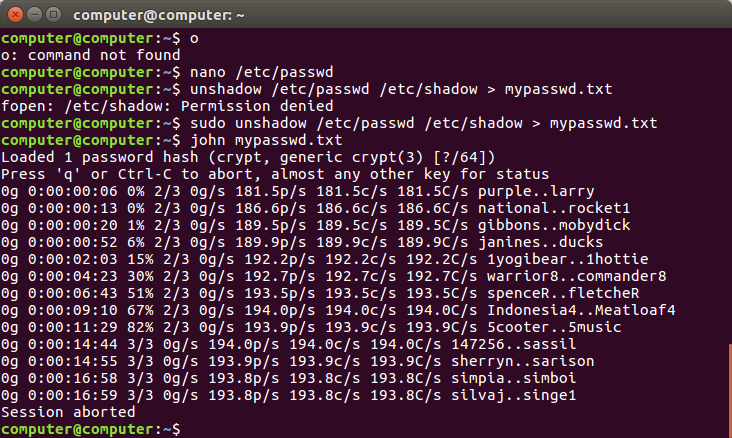
In this post I will show you how you can crack passwords with John the Ripper. We will start off by collecting the hashes from a linux machine, then use the tool unshadow and at last crack the hashes with John the Ripper. 1 – Collect hashes from a Linux machine We will start with collecting the hashes from the target machine. Run them against their respective file types to extract the password hashes:./zip2john./test.zip./zip.hashes./rar2john./test.rar./rar.hashes This will give you files that contain the password hashes to be cracked something like this:./test.zip:$pkzip$221001ba80c95e4e9547dcfcde4b8b2f05a80aaeb9d15dd76e7526b81803c8bf7201bf401ba808cbafdd390bf49ea54064ab3ff9f486e6260b9854e37d1ee3a41c54.$/pkzip$ After, that you can run John the Ripper directly on the password hash files.
John the Ripper – John the Ripper is an extremely fast password cracker that can crack passwords through a dictionary attack or through the use of brute force. SSH – The SSH protocol uses the Transmission Control Protocol (TCP) and port 22. Credentials and files that are transferred using SSH are encrypted. Most Linux systems.
- John the Ripper is one of the most popular password cracking tools available around. This free password cracking tool is chiefly written in C programming language. Encompassing a customizable.
- John the Ripper. It is a Password Cracking Tool, on an extremely fundamental level to break Unix passwords. Other than Unix-sort mixed passwords it also supports part Windows LM hashes and distinctive more with open source contributed patches. It is a free watchword softening mechanical get together made by and large up C. John the Ripper is unique in association with instruments like Hydra.
Most likely you do not need to install “John the Ripper” system-wide.
Instead, after you extract the distribution archive and possibly compile the source code (see below), you may simply enter the “run” directory and invoke John from there.
Compiling “John the Ripper”
Step 1: Download the latest version of ““John the Ripper”” and its signature
Step 2: Confirm the signature
This is a safety measure as we are dealing with dangerous thing.

Install the public key:
Check the signature:
You will see the message similar to the above. Ignore the warning as long as it says Good signature from “Openwall Project … “.
The warning is normal, see http://www.kernel.org/signature.html for more details.
Step 3: Uncompress and compile the sources
Note the make target for your system and type:
Where <system> is the appropriate make target. Alternatively, if your system is not listed, use:
If everything goes well, this will create the executables for John and its related utilities under “./run/”. Gilera runner st 125 engine manual.

Install the public key:
Check the signature:
You will see the message similar to the above. Ignore the warning as long as it says Good signature from “Openwall Project … “.
The warning is normal, see http://www.kernel.org/signature.html for more details.
Step 3: Uncompress and compile the sources
Note the make target for your system and type:
Where <system> is the appropriate make target. Alternatively, if your system is not listed, use:
If everything goes well, this will create the executables for John and its related utilities under “./run/”. Gilera runner st 125 engine manual.
Alternatively, you may copy the entire “run” directory to anywhere you like and use John from there.
Now you can change directory to there and test John, like this:
Installing “John the Ripper” on Ubuntu
Execute the next command to install “John the Ripper” on Ubuntu:
Crack Htpasswd John The Ripper Linux Download
Installing “John the Ripper” on CentOS/RHEL
Crack Htpasswd John The Ripper Linux Command
Execute the next command to install “John the Ripper” on CentOS/RHEL:
